What Makes A Blockchain Secure?
There are four key pillars to blockchain security: consensus, immutability, decentralization and cryptography. Compromising any one of these factors can leave a blockchain vulnerable to hacks and exploits.
Key Takeaways:
- The Proof-of-Work (PoW) and Proof-of-Stake (PoS) consensus mechanisms form integral components of blockchain security given they ensure data is legitimate and safeguard against 51% attacks.
- The immutability of blockchains means that no entity can alter individual blocks.
- The more people acting as validators on a decentralized blockchain, the harder it is to hack the protocol.
TABLE OF CONTENTS
The blockchain was introduced to the world in 2009 when Satoshi Nakamoto released Bitcoin’s distributed ledger. While many pundits associate blockchain solely with the cryptocurrency market, the reality is decentralized databases present a great number of security benefits for all matter of industries. This article will dive into what makes a blockchain secure, the potential ramifications for poor security measures, and how these networks can safely process billions of dollars in transactions.
Key Factors That Keeps The Blockchain Secure
The security of a blockchain is built atop the framework of four unique, but equally important concepts.
1. Consensus
In essence, consensus mechanisms form the guidelines for how a new block is added to the chain. This process is vital to how a distributed ledger works – without it, blockchain networks would be far less secure.
Most crypto networks use a series of independent blockchain nodes being operated from all over the world. For a new transaction to be verified on a blockchain, these blockchain nodes must “agree” that the new information is valid before it can be added to the chain. There are some instances where one node has a higher authority than others and can override consensus. However, this more centralized model is relatively uncommon and has other fail safes in place to avoid compromising data.
Several consensus mechanisms exist, each with a unique methodology for protecting the blockchain and ensuring that new data being approved is legitimate. However, the two most popular appear frequently throughout the crypto sphere and are generally regarded as being quite safe.
Proof of Work (PoW)
Proof of Work is the original consensus mechanism used by the Bitcoin blockchain. This form of securing the network is commonly associated with “mining”. Each “miner” is running an independent node of the Bitcoin server on their PCs, which are trying to solve a complex mathematical algorithm. The first computer to solve the equation is allowed to add the next block of transactions to the chain and receive the network’s native currency as a reward (e.g., BTC).
Proof of Work is an excellent disincentive for crypto hackers. Firstly, getting started mining Bitcoin is an extremely energy, time, and cost-expensive process. This immediately puts a barrier on who can get involved in such an attack. On top of this, a particularly common attack – the 51% attack – is incredibly difficult to hack on Bitcoin. A 51% exploit is only successful when one party gains control of more than half of a blockchain’s nodes. That way, they can achieve consensus on fabricated transactions and steal a large sum of crypto.
However, the resources required to own 51+% of the Bitcoin network are almost unthinkable, given the colossal and competitive nature of the blockchain. It would require thousands upon thousands of mining rigs, and even if a few nodes misbehaved, the Bitcoin blockchain would still operate as normal. The same principles apply to other PoW protocols too, although not quite as strictly.
Proof of Stake (PoS)
Proof of Stake is another key consensus mechanism for blockchain networks, growing substantially in popularity through the late 2010s. This mechanism was created as a more environmentally sustainable alternative to Proof of Work blockchain protocols. PoS systems work by selecting a node to validate the next block on a chain. Participating nodes must lock up a certain amount of cryptocurrency in a smart contract to dissuade malicious behavior. If a node operator is found to have validated a fraudulent transaction – or otherwise acted poorly – a fraction of their locked tokens will be destroyed.
The PoS consensus mechanism is considered slightly less secure than its PoW counterpart, for several reasons. PoS requires much less technical expertise and upfront cash to get started as a node operator. In addition, the ongoing electricity costs are significantly reduced. This makes it easier to coordinate an attack, especially on networks that are only operating a few nodes. This is how the Axie Infinity network was compromised in one of the blockchain’s biggest DeFi hacks – attackers gained majority control of the seven nodes responsible for verifying new transactions.
However, in practice PoS networks have proven to be very secure in their own right. Faults with this consensus mechanism tend to boil down to operational or design error, rather than any fundamental issue with the technology. Some even argue that PoS is actually better at dissuading 51% attacks than PoW alternatives. This is due to how crypto staking is compensated and the ramifications for “misbehaving”.
2. Immutability
Immutability is a vital concept to the long-term health of the distributed ledger ecosystem. The term sounds a little complex, but it is actually quite straightforward. Simply, immutability means that each time a new block is added to the chain, it is permanent. No entity can alter the network’s historic data, giving it a level of transparency missing from centralized databases like banks. Immutability is why investors can look up a Bitcoin transaction via a block explorer and rest assured the details they find are accurate.
The inability to tamper with the data on a blockchain provides several layers of security. For starters, people cannot lie about transactions made on a public blockchain. If they say they’ve sent 0.1 BTC to a certain address, this claim can be verified within seconds. Immutability also makes it hard for fraudsters to manipulate historic information and has merit for real-world use cases like auditing and distributing medical records.
3. Cryptography
Cryptography is how transactions, wallets, and smart contracts are all secured on a blockchain network. In a broader sense, cryptography refers to the study or act of writing and solving codes. When it comes to blockchain protocols, cryptography is a set of mathematical algorithms that are incredibly difficult to crack. There are two main types of cryptography used in securing a distributed ledger.
Hash functions
Cryptography, and specifically hashing, can be a tough concept to wrap one’s head around. In simple terms, hashing is an algorithm (hash function) that takes in a set of data and outputs it as a different value (hash). The output’s length depends on the hash function being used – for example, SHA-256 has an output of 256 bits.
Not only is hashing a form of encryption, it plays an important role in blockchain immutability. Each time a transaction is processed, a unique hash is attached to the corresponding block. This hash is intrinsically linked to the hash outputted for the previous block. Therefore, if a validator attempts to approve or manipulate blocks on the chain, other users on the network will quickly see the hash values change and can reject the bad actor.
Asymmetric cryptography
Asymmetric cryptography is a security system that revolves around the use of two related keys: a public and a private key. Those that have used a non-custodial cryptocurrency wallet will be familiar with these keys. Basically, the public key is used to encrypt data, while the private key is used to decrypt data. Without both of these keys working in harmony, transactions cannot be sent or received via a blockchain network.
Private keys create what’s known as “digital signatures” that allow investors to authenticate their ownership of coins being sent (or received). This string of data is then shipped off to a validator – a miner or staker – to ensure the transaction is legitimate. By pairing the digital signature with the sender’s public key, the node operator can approve the transaction if the data matches.
This form of encryption makes it much harder for hackers to access an individual’s portfolio. Many common encryption methods only require access to one key (e.g., a password), whereas asymmetric cryptography ensures access is restricted to those with the public-private key pair.
4. Decentralization
Decentralization is one of the blockchain’s pivotal philosophies – one that extends far beyond its security. When we think about major businesses in the financial sector (banks, governments, federal reserves, fund managers) all of their data and decision-making can be traced back to a central server or entity. Blockchains, on the other hand, spreads their database across hundreds (sometimes thousands) of copies of the network across the globe.
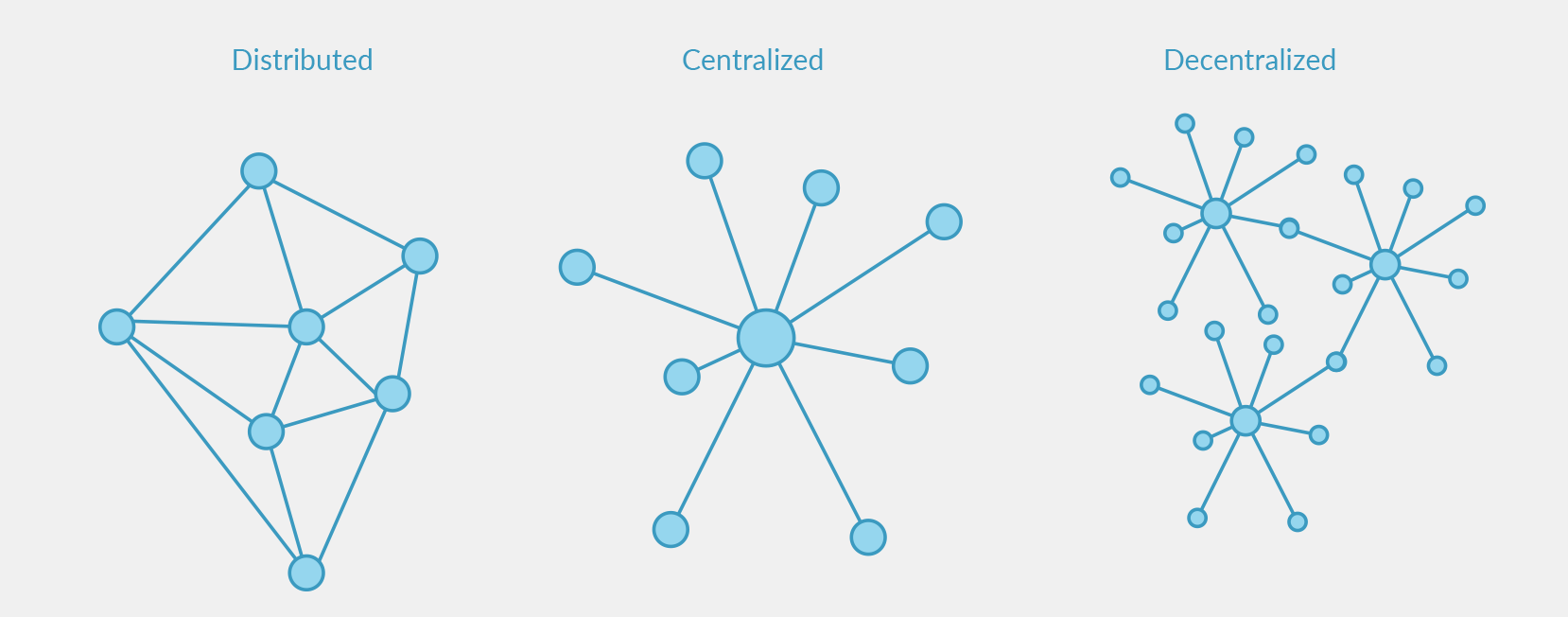
In a centralized system, if one person gains access to sensitive data, they can attack a single point of failure. This is not the case for decentralized databases. If one “copy” of the blockchain is compromised, it can easily be identified by other network participants and rejected.
Decentralization is incredibly important to a blockchain’s security. The greater the decentralization – that is, the more people participating as a validator on the network – the harder it is to hack the protocol. A truly decentralized network with thousands of independent ledgers is almost impossible to hack. However, this also grinds the blockchain’s scalability to a halt, so most systems must compromise a level of decentralization to ensure acceptable transaction speeds.
What Can Hackers Do?
A perfectly-designed blockchain is theoretically impossible to compromise. However, the technology is still relatively new and developers are figuring out how to best optimize these distributed ledgers. This has unfortunately led to hacks and exploits throughout the blockchain sector’s history.
- 51% attacks. Probably the most well-known form of attack, these occur when a malicious actor gains control of over 51% of a network’s nodes. If a group managed to band together enough resources to claim a majority of the network’s mining rigs, they could theoretically manipulate the database however they pleased. For example, in 2019 a hacker temporarily gained access to 51% of Ethereum Classic’s nodes. They double-spent on multiple crypto exchanges, resulting in a loss of $1.1m for the network. Experts believe the vulnerability came about due to the blockchain’s diminishing hash power, making it easy for a hacker to access a majority.
- Phishing and exploitation. Unfortunately, most blockchain “hacks” don’t have anything to do with the underlying technology. Phishing and other crypto scams are rife throughout the blockchain industry. Whether it’s legitimate-looking emails that are after a private wallet key or a pump-and-dump scheme promoted on social media, investors must be wary of where they enter sensitive information.
- Smart contract bugs. Smart contracts are programs that automatically execute when certain conditions are met. This technology is vital to the blockchain going forward and forms the framework of decentralized finance. However, these systems can occasionally invite bugs into a network, resulting in a potential exploit. One example occurred in 2021, when a hacker “tricked” a smart contract into depositing $30 million worth of Fantom coins into their wallet.
Blockchain Security In Real World Applications
The blockchain’s unique security mechanisms have quickly found their place in real-world applications among several industries.
Traditional Finance (TradFi)
Although the crypto market is a trillion-dollar industry, this figure pales in comparison to the amount of money that flows through financial institutions – think banks, fund managers, and brokers. Given the significant amount of money changing hands on a daily basis, some TradFi companies have turned to blockchain technology to improve their security measures.
- Goldman Sachs invests heavily in stablecoin USDC as a secure alternative to moving fiat currency internationally
- JP Morgan Chase uses blockchain tech to enhance the security and speed of large payments
- HSBC uses a blockchain to issue digital certificates and store digital assets
Health care
Distributed ledger technology has been posited as a potential solution to certain issues within the healthcare industry. Health care is an extremely sensitive sector that often requires the safe movement of private documents among professionals. Thanks to the blockchain’s immutability, historic data can be accurately distributed along a private network (assuming the network provides immutability as some private protocols do not).
The current process of a decentralized healthcare database works like this:
- A patient has a private medical record.
- Each time the patient must record medical information – be it a surgery, diagnosis, or doctor’s note, is hashed and appended to the blockchain.
- The data can only be accessed by those with the private key (the patient).
This makes it easy for patients to view health records and share only the relevant data with doctors, surgeons, and pharmacists.
Supply chain
The blockchain’s decentralized nature makes it a perfect solution for some of the supply chain industry’s historic issues. For starters, the immutability of most distributed ledgers ensures a level of transparency. This is vital to the smooth operation of supply chain and logistics companies, which require quality assurance for the products they are moving. This use case is directly linked to the healthcare industry too, as one of the supply chain’s biggest problems is the distribution of counterfeit medicine.
Blockchain allows both customers and supply chain businesses to track the journey of goods from their manufacturing point all the way to the customer’s doorstep. This helps ensure no tampering occurs at any step along the way and gives customers confidence they are receiving exactly what they purchased.
Conclusion
Blockchains are built to be one of the most secure technological systems in the world. The unique combination of cryptography, decentralization, and immutability combine to create a network that cannot be compromised by double-spending or fraudulent transactions. Additionally, blockchains can continue running even if one (or multiple) participants are disruptive – which is typically not the case when comparing crypto to traditional fiat currency systems.
That said, blockchain tech is still in its formative stages and is yet to realize its full potential. Although most networks are secure – particularly those with many nodes like Bitcoin and Ethereum – some have been exploited due to human error and coding oversights. But as the ecosystem continues to evolve, these issues will continue to be ironed out to create a safe and secure environment for investors.
Frequently Asked Questions
Can a blockchain be hacked?
Yes, a blockchain can be hacked, but it is extremely unlikely that powerful and popular networks like Bitcoin and Ethereum can be totally compromised. The computational power, time, money and other resources required to hack large blockchains are almost incomprehensible. However, human programming errors can and have been exploited in the past.
What is the most secure blockchain?
It’s difficult to definitively say one blockchain is more secure than another, but Bitcoin is likely the most secure. The asset’s extremely competitive nature, paired with its massive community, makes it almost impossible for a miner(s) to take majority control of the network. Bitcoin is one of the most decentralized cryptocurrencies in the world.
How is blockchain data secured?
Blockchain data is secured via a cryptography technique called “hashing”. Each time new data is processed by a distributed ledger, it runs through an encryption algorithm that both secures the information and helps keep a blockchain running at a reasonable speed.