The 10 Biggest DeFi Hacks In History (Updated List For 2025)
TABLE OF CONTENTS
Several crypto applications have been the target of significant hacks and exploits, which have resulted in the loss of billions of dollars worth of digital assets. This article will provide a list of DeFi hacks, thefts, and heists, including the biggest DeFi hack to date with a summary of lessons learned from such attacks.
DeFi Hacks Quick Summary
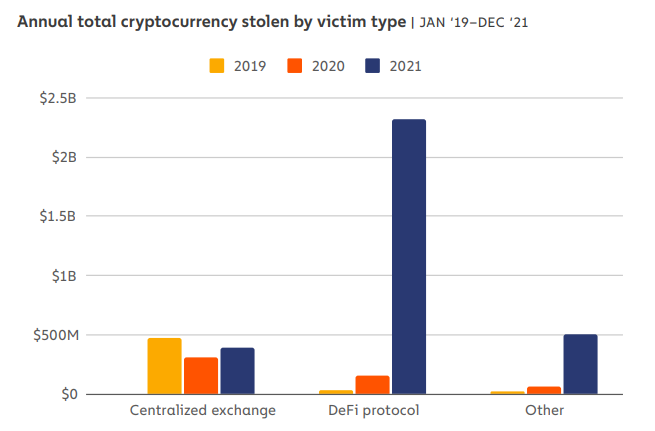
- In 2021, approximately $3.2 billion worth of cryptocurrencies were stolen. Of that, $2.2 billion (72%) were stolen from DeFi applications.
- The amount stolen from DeFi applications in 2021 increased by 1,330% in comparison to 2020.
- The amount stolen has continued to increase into 2022. Over $1.3 billion was stolen in the first quarter of the year.
- The most common method used to attack DeFi applications was flash loans.
- Flash loans have been used to manipulate both internal exchange rates and governance mechanisms.
- Private key security is also paramount when working with DeFi applications.
- DeFi users should thoroughly check all wallet permissions that are requested by a DeFi application, as these can sometimes be hacked.
- Experts within the industry suggest auditing the security of DeFi applications and smart contracts and assessing all third-party connections, including API keys, for vulnerabilities.
How Are DeFi Protocols Hacked?
The latest figures provided in the Chainalysis 2022 Crime Report indicate that hackers are now increasingly targeting DeFi-related protocols. During the first quarter of 2022, $1.3 billion worth of cryptocurrencies were stolen across the cryptocurrency industry. Of that $1.3 billion, 97% of cryptos were stolen from DeFi applications. These figures are significantly higher than crypto exchange hacks which have been declining over recent years.
Alongside the immense value locked in the ecosystem, DeFi applications are suitable targets for hackers due to the open-source nature of the underlying code. The majority of DeFi applications post the underlying code online. It can then be vetted by users and partners. This helps to build trust and allows for an increased level of composability that would be near impossible in traditional finance. However, the transparency of DeFi is also its main weakness.
DeFi crypto applications rely on a combination of programmable smart contracts that are executed on a blockchain. Smart contracts allow an application to function without the need to rely on human input. However, as smart contracts are a relatively new technology, errors within the code are common. As the code is open-source – for all the world to see – hackers and fraudsters have plenty of time to look for vulnerabilities.
List of DeFi Hacks
| DeFi Application | Date of Hack | Cause of Hack | Amount Stolen (USD) |
|---|---|---|---|
| Beanstalk | 18 April 2022 | Flash loans were used to manipulate governance mechanisms | $182 million |
| Ronin | 29 March 2022 | A connection to the developers of Axie Infinity, Sky Mavis, was exploited | $552 million |
| Wormhole | 3 February 2022 | The bridge between Ethereum and Solana was manipulated | $326 million |
| Vulcan Forged | 13 December 2021 | User’s private keys were stolen | $140 million |
| BadgerDAO | 2 December 2021 | Malicious code was added into the application, changing user’s wallet permissions | $120 million |
| bZx | 5 November 2021 | Private keys were stolen | $55 million |
| Compound | 30 September 2021 | A coding error was included with an upgrade | $150 million |
| Cream Finance | 27 October 2021 | Flash loan were used to manipulate exchange rates | $130 million |
| Poly Network | 10 August 2021 | The bridges of Ethereum, BNB, and Polygon were manipulated | $601 million |
| PancakeBunny | 19 May 2021 | Flash loan were used to manipulate exchange rates | $45 million |
Biggest DeFi Hacks – Explained
DeFi applications first entered the cryptocurrency industry between 2017 and 2018. Since then, hundreds of hacks have occurred. However, the following 10 hacks are the largest that have occurred during DeFi’s short lifetime.
1. Ronin Network ($650 million)
Ronin Network is a sidechain associated with the popular play-to-earn game, Axie Infinity. Initially developed on the Ethereum blockchain, developers decided to migrate Axie Infinity onto its own sidechain to alleviate congestion issues. Like Vulcan Forged, the blockchain-based game incorporates DeFi elements such as the ability to earn tokens from gameplay, and then use those tokens within the associated marketplace or to trade with other players. Although dominating the blockchain-based gaming sector for much of 2021, in March 2022 the game became the victim of the largest DeFi hack to date.
Similar to Wormhole and Poly Network, the Ronin hacker exploited vulnerabilities in the network’s bridge – the service that helps users move assets from Ethereum to Ronin. Due to the stealth-like nature of the attack, the stolen funds weren’t noticed missing until 6 days after the attack was completed. 9 validators are used to verify transactions that are processed across the Ronin Bridge. 5 validators must be in agreeance before funds are moved.
Sky Mavis, the company that created Axie Infinity, controlled 4 out of the 9 validators. Unfortunately, it also had access to another validator thanks to a previous agreement with the AxieDAO (Axie Decentralized Autonomous Organization). After compromising the systems of Sky Mavis, the attacker was able to control 5 of the 9 validators. With 5 out of the 9 validators under the attacker’s control,173,600 ETH and 25.5 million USDC were moved out of the Ronin Bridge contract. Digital assets totaled $650 million at the time of the incident.
Over $400 million in lost funds belonged to Axie Infinity users. To regroup those stolen funds, Axie Infinity investors, including Sky Mavis and Binance, raised $150 million to reimburse a partial amount. The number of validators required to control the Ronin Bridge was also upgraded to 21.
2. Poly Network ($601 million)
The Poly Network is a cross-chain application that focuses on interoperability. Like Wormhole, it allows users to move digital assets from one blockchain to another. In August 2021, the application was exploited for the second-largest DeFi hack ever, which totaled $601 million.
The Poly Network validates the transfer of assets between blockchains via Bookkeepers. The hacker noticed a vulnerability in Poly Network’s code that allowed them to replace the public key of a Bookkeeper which gave them control of a lock box. Once a lock box was controlled the hacker could execute any transaction that they wanted. The attacker then focused on assets held within the Binance Smart Chain, now BNB Chain, the Ethereum blockchain, and the Polygon network. $273 million was stolen from Ethereum, $85 million was stolen from Polygon, and $253 million was stolen from Binance Smart Chain.
Fortunately for Poly Network, the hack took an unusual twist after assets had been withdrawn. Like other DeFi hacking attempts, the Poly Network reached out to the attacker and offered them a bug bounty of $500,000 and also a position as Chief Security Adviser for the application. Although ignoring the job offer, the entire $601 million was returned to the Poly Network shortly after. In a subsequent Q&A session, the hacker stated that the plan had always been to hand back the stolen funds and that the hack was just to teach the Poly Network a lesson.
3. Wormhole ($326 million)
Wormhole is a multi-chain bridging platform that allows users to transfer crypto assets from one blockchain to another. Although Blockchain bridges are powerful tools, common vulnerabilities have been identified since their introduction in 2020 and 2021. Unfortunately, in February 2022, Wormhole was one of the first bridging platforms to have these vulnerabilities exploited. The platform lost $320 million worth of Wrapped Ethereum (WETH).
The attacker targeted the Wormhole bridge between the Ethereum and Solana blockchains. All transactions from one bridge to another must be approved by Wormhole ‘guardians’. The attacker found a way to forge these guardian signatures, which allowed them to trick the bridging system. By forging guardian signatures the hacker manipulated the system into thinking that 120,000 ETH had been deposited on the Ethereum side of the bridge. This allowed 120,000 wETH to be removed on the Solana side by the hacker.
After the hack, Wormhole developers offered the attacker a whitehat agreement. If the remainder of wETH were returned, the hackers could keep $10 million for finding the bug in Wormhole’s system. The hacker did not reply to the offer. To keep Wormhole operating, Jump Crypto, a cryptocurrency fund, replaced all 120,000 ETH.
4. Beanstalk ($182 million)
The fourth largest DeFi hack ever occurred in April 2022. Beanstalk, a protocol built on top of the Ethereum blockchain, was designed to offer a decentralized algorithmic stablecoin, called BEAN. Unfortunately, not long after it secured $150 million in funding and launched in September 2021, a flash loan attack managed to take advantage of the protocol’s governance mechanisms.
The attack on Beanstalk exploited an emergency function that allowed proposals to be implemented within 24 hours with a 2/3 vote. Using flash loan attacks, the hacker acquired a significant number of BEAN governance tokens that allowed them to control 79% of the voting power.
The voting power was then used to pass two proposals – Beanstalk proposals #18 and #19. The proposals transferred tokens from Beanstalk to both the attacker's address and also a Ukrainian donation address. Part of the sum sent to the attacker was then used to pay back the initial flash loan. Out of the $182 million stolen, $76 million was kept by the attacker.
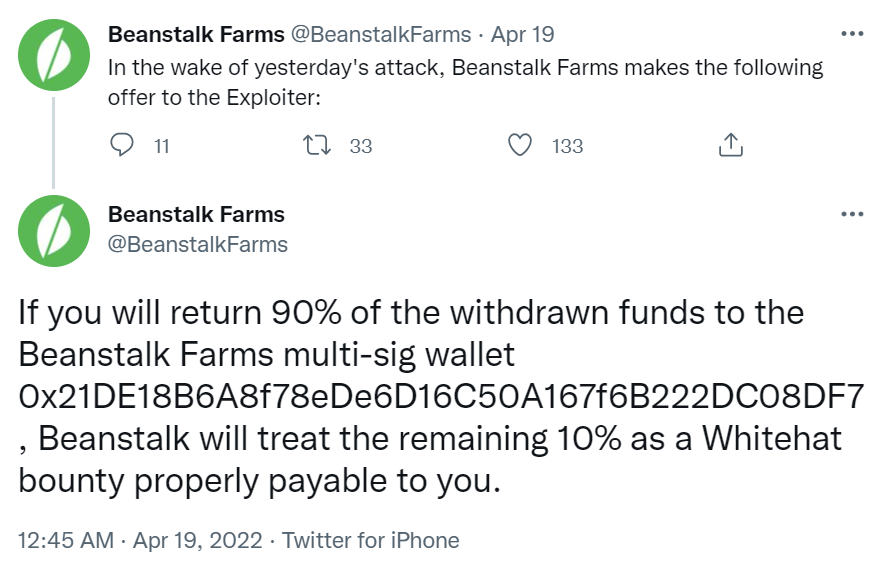
After the attack, Beanstalk offered a 10% bounty to the malicious party that exploited the app's governance mechanisms. The party would need to refund the remaining 90% of assets. Unfortunately, the exploiter did not take Beanstalk up on the offer. In June 2022, Beanstalk launched a re-funding effort called ‘The Barn Raise’ whereby participants could help to recapitalize Beanstalk by buying a secondary token called Fertilizer (FRT).
5. Compound ($150 million)
Compound is one of the oldest DeFi applications in the cryptocurrency industry. Launched in 2018, the popular lending and borrowing platform has amassed billions of value. After surviving three years in the DeFi ecosystem without any faults, in October 2021, an incorrect piece of code wrongly distributed over $150 million worth of native COMP tokens. Although the bug was introduced by a Compound upgrade, it could only be used by malicious parties that knew how to exploit the vulnerability.
Known as a ‘leaky tap’, the faulty smart contract within Compound Finance’s application distributed a significant number of native COMP tokens to users. The COMP tokens, which were originally intended for liquidity mining rewards, sat within a vulnerable liquidity pool. The pool of 280,000 vulnerable COMP tokens was worth $90 million at the time. The COMP tokens were then accessed by those who knew how to exploit the bug in the code.
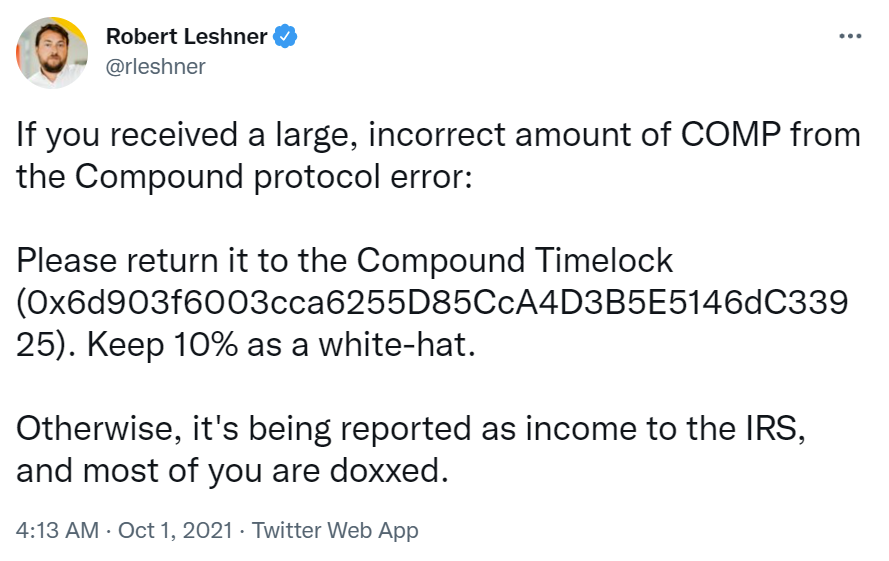
However, the decentralized nature of the application amplified problems. As changes to the application require agreeance by all community members, the incorrect distribution of tokens could not be halted until a new proposal had been passed. This took a week to implement. By the time a patch had been completed, a further 202,000 COMP tokens had entered the vulnerable liquidity pool, which meant a further $66 million was lost. Post the initial distribution, the founder of Compound Labs, Rob Leshner, took to Twitter to beg users to return wrongly distributed COMP funds. Just under half of all COMP tokens were returned.
6. Vulcan Forged ($140 million)
Vulcan Forged is a play-to-earn gaming platform that hosts a range of blockchain-based games. Rather than focus purely on decentralized finance, the Vulcan Forged gaming hub incorporates elements of DeFi into the ecosystem. Each game rewards players with tokens and then allows players to utilize those tokens to unlock more aspects of the game. The native token of the Vulcan Forged ecosystem is called PYR.
In December 2021, the Vulcan Forged ecosystem fell victim to an attack that resulted in the platform losing access to players’ private keys. To help manage customers’ funds, Vulcan Forged employed the services of Venly, a blockchain technology provider. Unfortunately, a weakness in Vulcan Forged servers became exposed, enabling a malicious party to access credentials for Venly. Using the credentials, the private keys of Vulcan Forged players were targeted.
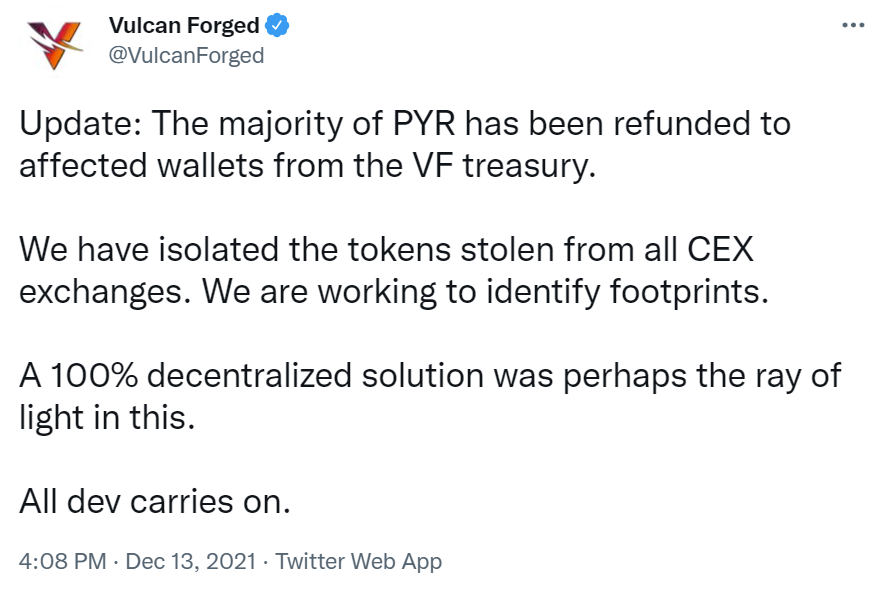
The attacker managed to steal the private keys for 96 wallet addresses in total. Cunningly, the attacker only targeted whales within the ecosystem, which meant that they were able to walk away with $140 million worth of PYR tokens (approx. 4.5 million tokens) by the end of the hack. On average, this equated to $1.46 million worth of tokens being stolen from each wallet. In the subsequent two months, the price of PYR crashed from $44 to $8. Fortunately for Vulcan Forged users, all of the 4.5 million PYR tokens were reimbursed.
7. Cream Finance ($130 million)
Cream Finance is a yield farming platform that enables unrestricted loans on crypto assets. Unfortunately, the platform fell victim to flash loan attacks in October 2021, which resulted in $130 million worth of cryptocurrencies being stolen. Cream Finance had previously lost $37 million in February 2021 and $29 million in August 2021. However, the October 2021 hack was to be the application’s largest. While $130 million is significant, the attack could have been much larger due to the platform’s close relationship with Yearn Finance. Fortunately, the attack was maintained to just the Cream Finance application.
According to ethical blockchain hackers, Halborn, the attack was orchestrated from two wallet addresses that targeted Cream Finance’s yUSD vault. Flash loans were initially borrowed using the two independent wallet addresses. Those loans were then used to interact with MakerDAO and Aave DeFi applications to generate large quantities of yUSD – a Yearn Finance liquidity provider token. After the acquisition of yUSD, a series of complex transactions were completed by the hacker so that a significant number of crYUSD tokens could be acquired. crYUSD is a Cream Finance liquidity provider token.
Using the vast quantity of crYUSD, the internal pricing of crYUSD was manipulated within Cream Finance to a point where the attacker held nearly $3 billion worth of crYUSD tokens. $2 billion worth of tokens were used to repay flash loans, and the remaining $1 billion was used as collateral to borrow from Cream Finance’s lending service. Over 15 different coins and tokens were loaned, totaling $130 million worth of value. The attacker then defaulted on all loans, leaving a $130 million hole in Cream Finance’s assets.
8. BadgerDAO ($120 million)
In December 2021, BadgerDAO, a DeFi protocol that allows users to bridge Bitcoin assets into the world of DeFi, suffered a hack that lost users $120 million. Unlike previous hacks, the attack did not involve exploiting smart contracts or private keys. Instead, the attacker manipulated BadgerDAO’s front-end platform. According to a BadgerDAO post-mortem blog post, at the time of the attack, BadgerDAO worked in partnership with a company called Cloudflare, which was brought in to improve the security of the platform. Unfortunately, it was this relationship that provided an opportunity for the hacker.
After compromising an Application Programming Interface (API) key associated with the Cloudflare account, the hacker was able to place new code into the BadgerDAO application. This code asked for new permissions from users when transactions were performed within the application.
Unknowingly, over 500 users accepted these new permissions, which allowed the attacker to transfer all of the assets held within those affected wallets to their own. The attacker managed to steal 2,100 BTC and 151 ETH from users in total, which at the time was worth $120 million.
9. bZx ($55 million)
bZx is a DeFi lending protocol that was launched in 2019. Unfortunately, the application has been hacked a total of 4 times since its launch. After suffering 3 crypto attacks in 2020, totaling approx. $9 million, the lending protocol suffered its fourth and largest attack in November 2021. The hack cost the platform $55 million.
bZx was designed to offer traders decentralized access to lending and crypto margin trading services using an innovative tokenized system. These services are split across the protocol’s Fulcrum and Torque front-end platforms. All crypto assets shared with the protocol entered global liquidity pools that were shared with a range of different exchanges. Although growing initially on Ethereum, bZx expanded to the Binance Smart Chain, now BNB Chain, and Polygon ecosystems. Unfortunately, the application lost control of a private key associated with assets deployed on the two new chains.
The hack began with a malicious email sent to a developer working on bZx. A file within the email ran a program that stole the seed phrase for the private keys associated with wallets held on the BNB and Polygon ecosystems. As a result, the hacker withdrew all stolen funds from the developer's personal crypto wallet, along with some of the platform’s funds. In total, $55 million was withdrawn.
10. PancakeBunny ($45 million)
PancakeBunny is a yield farming aggregator and optimizer that was originally built on the BNB Chain and later expanded to the Polygon ecosystem. It was designed to ease investors' yield generation process. On May 19, 2021, a hacker stole $45 million from the application and simultaneously caused the price of the native token, BUNNY, to lose 96% of its value.
According to a report from BunnyFinance, the company behind PancakeBunny, the attacker initially borrowed more than $700 million worth of BNB coins- the native coin of the BNB Chain. These BNB coins were borrowed from PancakeSwap using 8 different flash loans. PancakeSwap is one of the top decentralized exchanges that exist within the BNB Chain ecosystem.
Using the large amount of borrowed BNB, the hacker then manipulated the price of USDT/BNB and BUNNY/BNB liquidity pools on the PancakeBunny application. Through a complex set of transactions, the attacker was then able to acquire nearly 7 million BUNNY tokens, which were instantly sold for 2.4 million BNB. This caused the price of BUNNY to plummet from $240 to approx. $20. After the $700 million worth of flash loan BNB coins were repaid, the attacker was left with 114,631 BNB which at the time was worth $45 million.
Conclusion
DeFi is one of the quickest-growing ecosystems within the cryptocurrency industry. Unfortunately, with billions locked in the ecosystem, that value has drawn the eyes of many malicious parties. Due to the open-source nature of the ecosystem, hackers have been able to exploit DeFi applications using flash loan attacks, weaknesses in underlying code, and poorly formed governance mechanisms. The 10 biggest DeFi hacks, which have all occurred over the space of 2 years, have lost a cumulative total of nearly $2 billion.
According to security experts, DeFi applications are becoming more secure with each passing month. However, DeFi developers could do more to ensure funds remain secure. In particular, security audits and decentralized private key control are two methods that could have stalled the 10 largest attacks to date.